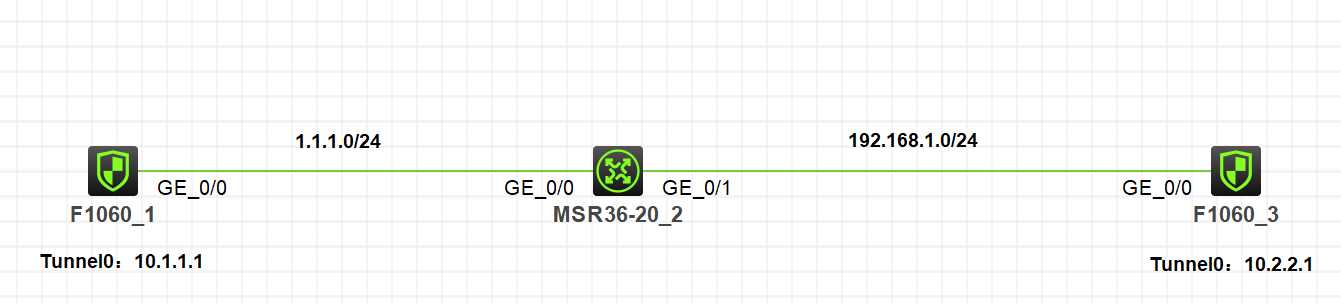
注:如无特别说明,描述中的 FW1 或 MSR1 对应拓扑中设备名称末尾数字为 1 的设备,FW2 或 MSR2 对应拓扑中设备名称末尾数字为 2 的设备,以此类推;另外,同一网段中,IP 地址的主机位为其设备编号,如 FW1 的 g0/0 接口若在 1.1.1.0/24 网段,则其 IP 地址为 1.1.1.1/24,以此类推
实验需求:
1.MSR2接口作nat server 映射内网地址10.2.2.1.
2.FW1和FW3建立IPsec隧道,涉及nat穿越.
3.不涉及安全域和安全策略
主要配置:
FW1:
#
interface LoopBack0
ip address 10.1.1.1 255.255.255.0
#
interface GigabitEthernet1/0/0
port link-mode route
combo enable copper
ip address 1.1.1.1 255.255.255.0
ipsec apply policy ply
#
ip route-static 10.2.2.0 24 1.1.1.2
#
acl advanced 3000
rule 0 permit ip source 10.1.1.0 0.0.0.255 destination 10.2.2.0 0.0.0.255
#
ipsec transform-set ts
esp encryption-algorithm aes-cbc-128
esp authentication-algorithm md5
#
ipsec policy ply 1 isakmp
transform-set ts
security acl 3000
local-address 1.1.1.1
remote-address 1.1.1.2
ike-profile pf
#
ike profile pf
keychain key
local-identity address 1.1.1.1
match remote identity address 1.1.1.2 255.255.255.255
proposal 1
#
ike proposal 1
#
ike keychain key
pre-shared-key address 1.1.1.2 255.255.255.255 key cipher $c$3$7tR4Xas8kMaW0BNkLtmL6SYAzYgdWUGDxw==
MSR2:
#
interface GigabitEthernet0/0
port link-mode route
combo enable copper
ip address 1.1.1.2 255.255.255.0
nat server global 1.1.1.2 inside 192.168.1.3
#
interface GigabitEthernet0/1
port link-mode route
combo enable copper
ip address 192.168.1.2 255.255.255.0
FW3:
#
interface LoopBack0
ip address 10.2.2.1 255.255.255.0
#
interface GigabitEthernet1/0/0
port link-mode route
combo enable copper
ip address 192.168.1.3 255.255.255.0
ipsec apply policy ply
#
ip route-static 1.1.1.0 24 192.168.1.2
ip route-static 10.1.1.0 24 192.168.1.2
#
acl advanced 3000
rule 0 permit ip source 10.2.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
#
ipsec transform-set ts
esp encryption-algorithm aes-cbc-128
esp authentication-algorithm md5
#
ipsec policy ply 1 isakmp
transform-set ts
security acl 3000
local-address 192.168.1.3
remote-address 1.1.1.1
ike-profile pf
#
ike profile pf
keychain key
local-identity address 192.168.1.3
match remote identity address 1.1.1.1 255.255.255.255
proposal 1
#
ike proposal 1
#
ike keychain key
pre-shared-key address 1.1.1.1 255.255.255.255 key cipher $c$3$OjYKsJVs/Q5wvdk9KNkK+aVUephZo6hZjQ==
验证:
FW1:
Ping 10.2.2.1 (10.2.2.1) from 10.1.1.1: 56 data bytes, press CTRL_C to break
Request time out
56 bytes from 10.2.2.1: icmp_seq=1 ttl=255 time=1.000 ms
56 bytes from 10.2.2.1: icmp_seq=2 ttl=255 time=1.000 ms
56 bytes from 10.2.2.1: icmp_seq=3 ttl=255 time=1.000 ms
56 bytes from 10.2.2.1: icmp_seq=4 ttl=255 time=1.000 ms
--- Ping statistics for 10.2.2.1 ---
5 packet(s) transmitted, 4 packet(s) received, 20.0% packet loss
round-trip min/avg/max/std-dev = 1.000/1.000/1.000/0.000 ms
Connection-ID Remote Flag DOI
------------------------------------------------------------------
1 1.1.1.2 RD IPsec
Flags:
RD--READY RL--REPLACED FD-FADING RK-REKEY
-------------------------------
Interface: GigabitEthernet1/0/0
-------------------------------
-----------------------------
IPsec policy: ply
Sequence number: 1
Mode: ISAKMP
-----------------------------
Tunnel id: 0
Encapsulation mode: tunnel
Perfect Forward Secrecy:
Inside VPN:
Extended Sequence Numbers enable: N
Traffic Flow Confidentiality enable: N
Path MTU: 1420
Tunnel:
local address: 1.1.1.1
remote address: 1.1.1.2
Flow:
sour addr: 10.1.1.0/255.255.255.0 port: 0 protocol: ip
dest addr: 10.2.2.0/255.255.255.0 port: 0 protocol: ip
[Inbound ESP SAs]
SPI: 1747129064 (0x682312e8)
Connection ID: 4294967296
Transform set: ESP-ENCRYPT-AES-CBC-128 ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843199/3513
Max received sequence-number: 4
Anti-replay check enable: Y
Anti-replay window size: 64
UDP encapsulation used for NAT traversal: Y
Status: Active
[Outbound ESP SAs]
SPI: 2898882926 (0xacc9716e)
Connection ID: 4294967297
Transform set: ESP-ENCRYPT-AES-CBC-128 ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843199/3513
Max sent sequence-number: 4
UDP encapsulation used for NAT traversal: Y
Status: Active
查看会话:
FW1:
Slot 1:
Initiator:
Source IP/port: 1.1.1.1/4500
Destination IP/port: 1.1.1.2/4500
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: UDP(17)
Inbound interface: InLoopBack0
Source security zone: Local
Responder:
Source IP/port: 1.1.1.2/4500
Destination IP/port: 1.1.1.1/4500
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: UDP(17)
Inbound interface: GigabitEthernet1/0/0
Source security zone: Untrust
State: UDP_READY
Application: GENERAL_UDP
Rule ID: 0
Rule name: any
Start time: 2021-11-04 21:27:00 TTL: 50s
Initiator->Responder: 7 packets 1052 bytes
Responder->Initiator: 30 packets 1509 bytes
Initiator:
Source IP/port: 1.1.1.1/500
Destination IP/port: 1.1.1.2/500
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: UDP(17)
Inbound interface: InLoopBack0
Source security zone: Local
Responder:
Source IP/port: 1.1.1.2/500
Destination IP/port: 1.1.1.1/500
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: UDP(17)
Inbound interface: GigabitEthernet1/0/0
Source security zone: Untrust
State: UDP_READY
Application: ISAKMP
Rule ID: 0
Rule name: any
Start time: 2021-11-04 21:27:00 TTL: 753s
Initiator->Responder: 2 packets 468 bytes
Responder->Initiator: 2 packets 408 bytes
MSR2:
Slot 0:
Initiator:
Source IP/port: 1.1.1.1/4500
Destination IP/port: 1.1.1.2/4500
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: UDP(17)
Inbound interface: GigabitEthernet0/0
Responder:
Source IP/port: 192.168.1.3/4500
Destination IP/port: 1.1.1.1/4500
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: UDP(17)
Inbound interface: GigabitEthernet0/1
State: UDP_READY
Application: GENERAL_UDP
Rule ID: -/-/-
Rule name:
Start time: 2021-11-04 21:28:30 TTL: 40s
Initiator->Responder: 7 packets 1052 bytes
Responder->Initiator: 35 packets 1785 bytes
Initiator:
Source IP/port: 1.1.1.1/500
Destination IP/port: 1.1.1.2/500
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: UDP(17)
Inbound interface: GigabitEthernet0/0
Responder:
Source IP/port: 192.168.1.3/500
Destination IP/port: 1.1.1.1/500
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: UDP(17)
Inbound interface: GigabitEthernet0/1
State: UDP_READY
Application: ISAKMP
Rule ID: -/-/-
Rule name:
Start time: 2021-11-04 21:28:30 TTL: 620s
Initiator->Responder: 2 packets 468 bytes
Responder->Initiator: 2 packets 408 bytes
Total sessions found: 2
FW3:
Slot 1:
Initiator:
Source IP/port: 1.1.1.1/4500
Destination IP/port: 192.168.1.3/4500
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: UDP(17)
Inbound interface: GigabitEthernet1/0/0
Source security zone: Trust
Responder:
Source IP/port: 192.168.1.3/4500
Destination IP/port: 1.1.1.1/4500
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: UDP(17)
Inbound interface: InLoopBack0
Source security zone: Local
State: UDP_READY
Application: GENERAL_UDP
Rule ID: 0
Rule name: any
Start time: 2021-11-04 21:28:30 TTL: 47s
Initiator->Responder: 6 packets 892 bytes
Responder->Initiator: 39 packets 1901 bytes
Initiator:
Source IP/port: 1.1.1.1/500
Destination IP/port: 192.168.1.3/500
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: UDP(17)
Inbound interface: GigabitEthernet1/0/0
Source security zone: Trust
Responder:
Source IP/port: 192.168.1.3/500
Destination IP/port: 1.1.1.1/500
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: UDP(17)
Inbound interface: InLoopBack0
Source security zone: Local
State: UDP_READY
Application: ISAKMP
Rule ID: 0
Rule name: any
Start time: 2021-11-04 21:28:30 TTL: 547s
Initiator->Responder: 2 packets 468 bytes
Responder->Initiator: 2 packets 408 bytes
Total sessions found: 2
触发需要公网一侧,因为内网测无法找到对端.
以上就是企业组网配置方案-IPSec主模式NAT穿越(涉及DNAT)的介绍。如果你还有其他问题,欢迎进行咨询探讨,希望桂哥网络的专业的解决方案,可以解决你目前遇到的问题。桂哥网络提供全球主机托管、服务器租用、MPLS专线、SD-WAN等方面的专业服务,资源覆盖全球。欢迎咨询。
TikTok千粉账号购买:https://www.tiktokfensi.com/

TOP